What Is WebRTC Leak and How Can You Protect Yourself From It?

Table of contents
What Is WebRTC?
Simply put, WebRTC (Web Real-Time Communication) is an open-source project that provides most browsers with a feature that allows voice, video chat, and P2P sharing to occur without any additional extensions or add-ons being used.
WebRTC is usually pretty useful, but it can be detrimental to your online privacy if you are using a VPN and experience a WebRTC leak.
What Is WebRTC Leak?
A WebRTC leak is a vulnerability that leaks your real IP address when using a VPN. How does WebRTC know your IP address? Well, it uses the ICE (Interactive Connectivity Establishment) protocol to discover it, and it also uses STUN/TURN servers which can actually see your IP address just like websites can.
Basically, here’s what the problem is:
Web browsers tend to implement WebRTC in such a way that it allows them to send requests to STUN servers which will return your local and public IP address. What’s more, the requested results are available in Javascript, making them much more accessible.
Even worse, the requests are made outside the normal XMLHttpRequest process – an API that transfers data between a web browser and a web server. Because of that, the requests can’t be seen in the developer console. Also, they can’t be blocked with plugins like Ghostery or AdBlockPlus.
It’s important to understand that a WebRTC leak isn’t an issue with the VPN service itself, but with the web browser you’re using.
Why Is a WebRTC Leak Dangerous?
The answer is pretty simple – if your IP address is leaked while connected to a VPN service, that makes it much easier for the government to spy on you, your ISP to track your activities, and cybercriminals to exploit your sensitive data. Not to mention it completely defeats the purpose of using a VPN in the first place.
Plus, consider this – all it takes is a few Javascript commands for a website to find out what your real IP address is. Not only is that dangerous to your privacy like we just mentioned, but it will also prevent you from accessing geo-blocked content.
And lastly, since the STUN requests can’t be seen in the developer console or blocked with various plugins, they can be easily tracked online by advertisers if they set up and configure their own STUN server that uses a wildcard domain (also called a wildcard DNS record).
How to Test WebRTC Leaks
The process is relatively simple – just do the following:
- Run your VPN and connect to a server.
- Next, use the WebRTC Leak Test Tool provided by BrowserLeaks while connected to the VPN server.
- If you see your real public IP address displayed in the results, you have a WebRTC leak.
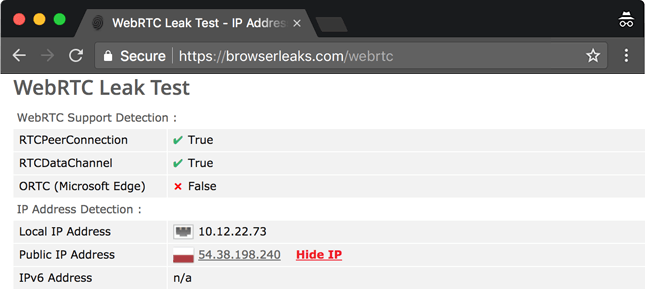
You might also notice that – sometimes – test results show your internal/local IP address too (usually in the following format – 10.x.x.x. And 192.x.x.x.). We recommend not worrying about that since the only thing that matters when trying to detect a WebRTC leak is the public IP address.
If you’d like to try out other tests that cover WebRTC leaks, here are some options:
Also, if you’d like to learn about other ways to test VPN connections, here’s an in-depth guide we wrote on the topic.
How to Fix and Prevent WebRTC Leak Issues
Here are three things you can do to solve this problem:
1. Disable WebRTC in Your Browser
Firefox
If you use Firefox, you’ll be happy to know you can directly disable WebRTC in it with ease.
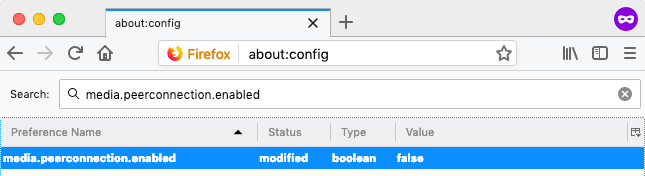
Here’s what you need to do:
- Start up Firefox.
- Type “about:config” in the URL bar.
- Hit Enter and click on “I accept the risk.” Don’t worry about the warning.
- Now, type “media.peerconnection.enabled” in the Search bar.
- Under the Search bar, look for the “Preference Name” tab.
- Double-click the item that’s displayed to change the value to “false.”
If you are a CactusVPN customer, you can use our Firefox extension to easily disable WebRTC.
Google Chrome on Android
If you have Chrome on mobile, you can disable WebRTC manually on it too. Just type in or copy the following URL in a Chrome tab:
“chrome://flags/#disable-webrtc”
Once the page is loaded, just scroll down, look for “WebRTC STUN origin header,” and disable it. While not necessary, you can also disable the “WebRTC hardware video encoding” and “WebRTC hardware video decoding” options if you want to be extra safe.
Brave
The Brave browser is also susceptible to WebRTC leaks since it’s based on Chromium. The easiest way to fix the problem is to do the following:
- Head to “Preferences.”
- Click on “Shields.”
- On the right, look for “Fingerprinting Protection.”
- From the drop-down menu, select “Block all fingerprinting.”
If that doesn’t work for you or you want to try something else, an alternative way to stop WebRTC leaks on Brave is to go to “Preferences>Security>WebRTC IP Handling Policy” and just select “Disable Non-Proxied UDP.”
2. Use Add-Ons and Extensions to Disable WebRTC
In the case of browsers where WebRTC can’t be disabled, you need to use third-party browser add-ons and extensions to solve the problem. Here’s a quick overview of your options:
- Google Chrome – With Chrome, it’s best to either use WebRTC Leak Prevention or uBlock Origin. You can also use them together if you want. If you are a CactusVPN customer, you can use our Chrome extension.
- Opera – Your best option is to use the WebRTC Leak Prevent add-on. Once installed, head to the advanced options (in the add-on), and select the “Disable non-proxied UDP (force proxy)” option. You can also use uBlock Origin since there now is an Opera add-on for it.
One thing we really need to emphasize is that add-ons and extensions aren’t always 100% fool-proof. There’s always a very small chance that you might still be exposed to a WebRTC leak when using them, so keep that in mind.
Of course, you could always just stop using the browsers that don’t let you disable WebRTC directly altogether. If you really need to use one, though, we’d recommend picking Opera over Chrome.
3. Use a VPN Service With WebRTC Leak Protection
Even though the WebRTC leak issue is a problem you mostly need to worry about if you use a VPN service, you can solve and prevent it with a different VPN service – as long as the provider can guarantee they offer complete WebRTC leak protection. In this case, it really helps if they offer a free trial so that you have time to thoroughly test the connections to make sure no leaks occur.
As a general rule of thumb, free VPN services should be avoided if you want to make sure you get the WebRTC leak protection you want.
Looking for a VPN That Offers Top-Notch WebRTC Leak Protection?
We’ve got you covered – we ran multiple tests on CactusVPN connections while using the solutions mentioned above to make sure they don’t experience any WebRTC leaks.
Plus, that’s not the only way we protect your privacy. We also use high-end encryption (AES), we don’t log any of your data, we offer DNS leak protection, and we provide access to six VPN protocols: OpenVPN, SoftEther, SSTP, IKEv2/IPSec, L2TP/IPSec, PPTP.
Enjoy Our Service on Multiple Devices
We offer user-friendly VPN apps you can quickly install on various platforms: Windows, macOS, iOS, Android, Android TV, Amazon Fire TV.
Also we offer browser extension for Chrome and Firefox.

Special Deal! Get CactusVPN for $3.5/mo!
And once you do become a CactusVPN customer, we’ll still have your back with a 30-day money-back guarantee.
What Is WebRTC Leak? The Bottom Line
A WebRTC leak is a vulnerability that can occur in multiple web browsers (Firefox, Google Chrome, Brave, Opera) which can leak your real IP address when you are connected to a VPN service.
Luckily, it’s pretty easy to detect WebRTC leaks, and you can quickly fix the problem on all browsers. Choosing a VPN service that offers WebRTC leak protection helps as well.
 Using a VPN on a Router
Using a VPN on a Router
 VPN Obfuscation (Full Guide for Beginners)
VPN Obfuscation (Full Guide for Beginners)
