What Is Anonymous Browsing and How to Be Anonymous Online

While the Internet is an almost endless source of entertainment and information, it’s hard not to wonder just how safe it is overall. After all, all that convenience has to come with a price, right? You’re correct, and that price seems to be your privacy.
Well, that’s where anonymous browsing comes into play - the idea of surfing the web without leaking any personal information about yourself, and having it logged by governments, advertisers, and other businesses.
Table of contents
- Why Is Anonymous Browsing Important?
- It Keeps Government Surveillance at Bay
- It Protects Your Right to Free Speech
- It Prevents Search Engines From Getting Too “Friendly”
- It Keeps Sensitive Data Out of Advertisers’ Hands
- It Prevents ISP Bandwidth Throttling
- It Keeps Your Data Safe on Unsecured Networks
- It Lets You Access Restricted Content
- It Makes Torrenting Safe
- How to Be Anonymous Online – The Basics
- How to Be Anonymous Online – The Next Level
- Conclusion
The good news is that something like that is achievable, but before we start discussing how to be anonymous online, we do need to make one thing clear – there really isn’t such a thing like 100% online anonymity. You can definitely take precautions to protect your privacy and significantly reduce the risk of your personal data being leaked or exposed, but no approach is completely foolproof given how extensive, versatile, and risk-prone the Internet is.
So, when we’ll be using terms like “anonymous browsing” or “anonymous surfing,” that’s the kind of thing we’ll be referring to.
Why Is Anonymous Browsing Important?
Believe it or not, it’s getting harder and harder to enjoy any kind of privacy on the Internet. What you do online doesn’t really just stay between you and your device. But to get more specific, here are some reasons why you need private browsing so much:
1. It Keeps Government Surveillance at Bay
Governments know what a valuable source of information the Internet is, and they treat it accordingly – by trying to snoop on anything they can, of course.
And while you might think that government surveillance only happens in the US, the reality is far from it. While the US has dozens of mass surveillance projects, it’s not the only country to do that.
Also, keep in mind that most governments require national ISPs to make user data available to the authorities, and store it up to a certain number of years.
Anonymous browsing would help with this by making it harder for government agencies to keep tabs on what you do online, and monitor your online traffic. Still, it’s worth noting that it won’t protect you 100% from surveillance. As long as you’re on the Internet, that’s just not possible.
2. It Protects Your Right to Free Speech
While almost all countries in the world grants their citizens the right to freedom of speech, it’s starting more and more to look like a theoretical right. In reality, it’s pretty easy to have your free speech taken away – whether it’s an online platform censoring you, or people cyber bullying you for your opinions.
Sometimes, even the legal system doesn’t have your back. In countries like Saudi Arabia, for example, where self-censorship is the norm. Otherwise, you risk getting into serious legal trouble – from being thrown in jail to getting flogged in public.

Well, the good thing about anonymous surfing is that it can give you a voice on the Internet – even if you don’t have one. Since people won’t know who you are, you’ll be able to speak your mind freely – whether you’re debating social, political, or economical issues (just to name a few).
3. It Prevents Search Engines From Getting Too “Friendly”
There’s no denying search engines have made the Internet much more user-friendly and convenient, but are you aware of the cost? Those autocomplete results you get when you type in a letter or a word that seem awfully familiar aren’t just a nice feature – they’re complex algorithms that use personal info from you to deliver more personalized results.
What kind of information, you ask? Well, search engines like Google, Yahoo!, and Bing collect the following:
- The websites you search for and access
- Your geo-location
- Your age and gender
- Browsing history from any third-party app/website that relies on a search engine’s services
- Any voice commands you issue to a Voice Assistant that’s owned by them (like Google Assistant)
- Email contents (in the case of search engines that offer email services)
- Device information
- How you look (some search engines use facial recognition in their photos)
- Your religious and political beliefs
- How healthy you are
- Everywhere you’ve been
- Who your friends are
And that’s just scratching the surface.
What’s more, all that data is also integrated alongside other bits of info collected through services the search engines own (like YouTube, which is owned by Google).
While anonymous browsing can’t protect you against every single breach of privacy we listed above, it can help you better protect your personal data to enjoy more privacy and being able to use search engines without that creepy “I know everything about you” feeling.
4. It Keeps Sensitive Data Out of Advertisers’ Hands
Like search engines, advertisers know a little too much about you as well. How, you ask? Well, you can thank search engines and social media platforms for that (along other smaller websites). They share your data with third-party advertisers to make a profit.
And no, it’s not a big secret or illegal – it’s very likely mentioned in the search engine or social media website’s Terms of Service. Hey, those are usually free-to-use platforms, so this isn’t a huge surprise.
But they aren’t the only culprits. ISPs can sometimes sell user data to third-party advertisers too. Fortunately, it doesn’t happen in all countries. For now, only people in the US have to deal with this (though, there’s no guarantee that shady, behind-the-scenes ISP-advertiser deals aren’t happening in other countries).
What does all this mean for you? Besides having your privacy sold for a profit, it means you’ll start seeing more and more personalized ads on the web. For instance, if you like a Facebook page about stoves, don’t be surprised if you’re going to start seeing stove ads on Facebook, Google, and other websites.
For some people, that can be convenient. For most of us, it’s just creepy and intrusive.
Luckily, private browsing can help with this by limiting the amount of info advertisers get about you. Also, it’s a good idea to check the Privacy Settings on most platforms and search engines you use to disable personalized ads (or anything related to ads, really).
5. It Prevents ISP Bandwidth Throttling
ISPs can actually slow down your connection speeds if they consider you are using “too much data” to do something online – be it streaming, VoIP calls, or gaming. They allegedly do that to improve their services (which is believable), but they’re also doing it to convince users like you to pay for a bigger, pricier data plan or get a more expensive subscription.
ISPs can do that because they can monitor everything you do on the Internet. The good news is you can fight back by surfing the web anonymously to make sure your ISP can’t keep tabs on what websites you access or what files you download.
6. It Keeps Your Data Safe on Unsecured Networks
Using WiFi that requires no password on the go is extremely convenient, but it’s also very dangerous. Due to the lack of encryption, anyone can eavesdrop on your connections and snoop on your online activities and personal details (like credit card numbers and login credentials).
While you could avoid that by just using a password-protected network instead, the unfortunate truth is that doing that isn’t guaranteed to be safe either. Why? Because of the KRACK vulnerability that can compromise WPA2-secured networks.
The best option is to just make sure you’re enjoying a certain degree of anonymity when you’re connecting to a WiFi network – secured or unsecured. This way, even if someone were to monitor your connection, they won’t be able to learn anything valuable or steal any sensitive info.
7. It Lets You Access Restricted Content
While the Internet offers a nearly vast array of content, you can’t actually enjoy all of it. A lot of times, geo-restrictions will get in the way, preventing you from doing that. In short, they are a method of blocking access to content based on your geographical location. They’re generally used by content providers for legal, network, and copyright-related reasons.
Netflix is a pretty good example of that. While the service is mostly available worldwide, its US content library cannot be accessed by online users outside the United States. The website checks your IP address when you connect to it, and redirects you to the “appropriate” library.
Geo-restrictions aren’t your only concern, though – online content can be restricted through the use of firewalls. That usually happens when a government wants to block certain websites (like how China blocks Google, Facebook, and Blogspot), or when a workplace/learning institution wants to make sure its employees/students don’t “slack off” by browsing online content (like YouTube or Twitter).
In both situations, anonymous browsing would allow you to bypass firewall restrictions without anyone knowing most of the time.
8. It Makes Torrenting Safe
Depending on the country you live in, downloading torrents can be a hassle-free thing you do on the Internet, or it can be an illegal activity that can lead to you receiving DMCA notices, getting fined thousands of dollars (if not more), and even potentially landing in court or jail.
Even if we leave the legal aspect aside, torrenting is still not very safe because everyone else who is downloading/uploading the same torrent as you can pretty much see your real IP address, meaning any private data associated with your IP is left at the mercy of strangers.
Fortunately, anonymous browsing helps you overcome this hurdle by making sure nobody knows your identity – both to keep you safe from potential hackers and copyright trolls, and from getting in trouble with the law.
As a clear disclaimer: we don’t endorse intentional copyright infringement or illegal online piracy, but we do understand some people can only access entertainment, work, or school files through P2P.
How to Be Anonymous Online – The Basics
In this section, we’ll be covering the more easier and common ways to retain your anonymity when you’re on the Internet. That’s not to say they are not efficient, of course.
1. Use a VPN (Virtual Private Network)
A VPN is a service you can use to surf the web anonymously by masking your real IP address and encrypting your online traffic to make sure nobody can monitor it. Due to how easy it is to use a VPN, it’s one of the most popular methods of anonymous browsing.
Advantages
- A VPN’s encryption can prevent cyber criminals, government surveillance agencies, and ISPs from keeping tabs on what you do online and stealing sensitive data from you. Basically, if they try to monitor your traffic, they’ll just see gibberish – even on unsecured networks.
- VPNs make it easy for you to access unrestricted content by masking your IP address and – consequently – your geo-location. Neither geo-restrictions or firewalls will be able to stand in your way.
- VPNs generally rely on shared IP technology (multiple people using the same IP to connect to the web) to protect user anonymity, essentially ensuring nobody can trace the connection to one user.
- A VPN is normally very easy to set up because there are plenty of third-party providers that offer VPN clients that work across numerous platforms.
Disadvantages
- A VPN’s encryption and the distance between you and the server might sometimes interfere with the connection speed, meaning you might experience slower speeds, though that doesn’t happen all the time.
- VPN clients don’t work on devices that don’t have native VPN support – like gaming consoles, for example.
- Proper VPN services are not free, though the costs are usually pretty low. While you could use free VPNs, the drawbacks are just not worth it since they only endanger your privacy instead of protecting it.
Need a Reliable VPN?
If you want to enjoy anonymous browsing with a VPN, CactusVPN has got your back. We offer an affordable VPN service that uses high-end AES encryption to secure your private data and online traffic whenever you’re on the Internet. Also, we have a strict no-log policy, meaning we don’t store any sensitive info about our users.
Our 30+ high-speed servers all use shared IP tech, and come equipped with unlimited bandwidth. What’s more, our VPN apps are very user-friendly.
Plus, if you’re interested in accessing geo-blocked content, you’ll definitely like that our VPN can come bundled with a Smart DNS service that can help you unblock over 300 geo-restricted websites from around the world.
Special Deal! Get CactusVPN for $3.5/mo!
And once you do become a CactusVPN customer, we’ll still have your back with a 30-day money-back guarantee.
2. Use a Proxy
A proxy is a server that acts as an intermediary between a small local network and the Internet. Many online users rely on proxies to hide their IP addresses and access geo-blocked content. Most proxy services are generally free, but there are also paid proxies.
Advantages
- Using a proxy to access websites can be quite fast due to the service’s caching ability (storing websites users visit for later, basically) meaning you’d probably get reduced load times.
- Proxies are easy to use, and they hide users’ IP addresses to help them browse the web anonymously.
- Depending on the proxy admin’s preferences, a proxy server can be set to automatically filter out malicious websites.
Disadvantages
- Despite the caching feature, if the proxy server is overcrowded, you might experience slower speeds. This tends to happen with free proxies a lot.
- Most proxies just hide your IP – they don’t use encryption to secure your Internet traffic, meaning you can’t rely on them to truly protect your privacy, so much so if you’re using an unsecured network. While some proxies might use SSL encryption, it isn’t the most secure one out there – not to mention the NSA can allegedly intercept and crack it.
- Lack of encryption aside, proxies can’t really deliver complete anonymity simply because the owner of the proxy server will always know what your real IP address is if you use HTTP connections.
3. Use Tor (The Onion Router)
Tor is essentially an anonymity network that allows users to access the web in a more private manner. It works by passing data between multiple relays (also called “routers” or “nodes”) as a means to conceal a user’s online traffic and location.
Advantages
- Any websites you access with Tor can’t track your IP address. At the same time, any websites you visit cannot be traced back to your IP address.
- It’s extremely difficult for government agencies to shut down Tor completely because it’s a network that’s distributed over numerous countries.
- Tor is pretty simple to set up, and it works on multiple platforms. It’s also free to use.
- Since your online traffic is sent to multiple relays (whose operators don’t know the source of the traffic), web packets can’t be associated with a specific online user.
Disadvantages
- While Tor’s number of relays seems pretty high (over 7,000), it’s not enough to keep up with the number of users. Thus, using Tor means having to often deal with slower connections.
- It is possible for an ISP to block a Tor relay if it spots it. Even countries can do that, with China being a good example. When that happens, it’s more difficult for you as a Tor user to connect to the web.
- While Tor is pretty secure in general, it still has its weaknesses. At one point, its Mac and Linux clients had a vulnerability that could potentially leak user IPs. The FBI also managed to hack numerous Tor users (for good reason) by using a non-publicly known Tor vulnerability.
- The nodes are run by volunteers, which means your privacy is often at the mercy of human error.
- The last relay Tor traffic passes through before reaching its destination is known as an exit relay. Unfortunately, exit relays don’t really use any encryption since they are responsible for decrypting the traffic. That pretty much means that whoever is running the exit relay can easily monitor all the traffic passing through it.
4. Use Incognito/Privacy Mode on Your Browsers
Most popular browsers come with an Incognito/Privacy mode. The idea is to use it if you don’t want any data that’s related to your current session to be stored. In theory, that means no web cache, cookies, or web history are used.
However, keep in mind that this feature is best used alongside a privacy tool like a VPN. Privacy/Incognito modes offer a certain degree of anonymous browsing, but they don’t secure your connection. Also, the privacy is on your end only.
5. Clear Your Cache Regularly
One of the main reasons you should clear your browser’s cache is to get rid of all the cookies that are placed on your device when you browse online. If you’re not familiar with cookies, they are small text files that are placed on your computer when you visit a website (don’t worry – you are often asked to give your consent for that).
Cookies are used to store info about your browsing habits, so that websites can offer you a more personalized and convenient experience (like not requiring you to re-enter your login credentials, or storing your shopping cart items for a while even if you abandon the cart).
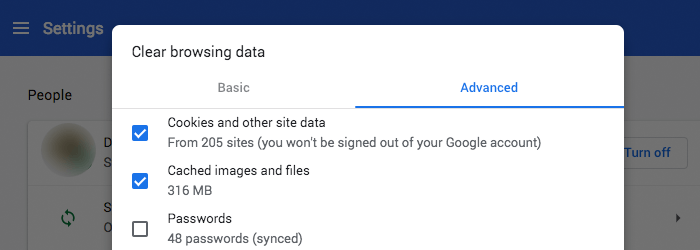
Usually, that isn’t a huge concern. However, the fact that cookies can be used by advertisers to track your online movements can be pretty annoying – not to mention a breach of your privacy. Plus, according to Cookie Central (a large resource on Internet cookies), unscrupulous third parties can actually use cookies in a way that lets them “build detailed profiles of your interests, spending habits, and lifestyle.”
While you can’t get rid of cookies entirely, you can clear your web browser cache regularly to make it harder for websites to track your habits. If you want to be extremely diligent, you could clear your cache after every web session.
Besides helping with cookies, clearing your cache might also improve loading speeds and fix browser errors.
6. Use Ad Blockers
Google allegedly displays around 29 billion ads per day to online users. And that’s only Google – we’re not taking platforms like Facebook into account.
“Alright, so I might get spammed with tons of ads on a daily basis, but that’s not such a huge problem.”
True, that might not seem problematic, but consider this – online ads aren’t just simple text boxes that are only for show. They actually “listen” to what you’re doing – basically monitoring your clicks and actions to follow you on the Internet. Why? So that you can be served even more “personalized” ads, of course.
And no, that’s not considered illegal.
Plus, besides the invasion of your privacy, some ads can also contain malware, easily infecting your device if you engage with them.
That’s why you should always have an adblocker on your browser. Here are some recommendations:
We highly recommend uMatrix because it doesn’t just block ads, but also unwanted scripts, iframes, and other browser requests, and you have complete control over everything.
The plugins work on most browsers. Sometimes, they might have different names but they accomplish the same goal.
And while we’re on this topic, you should consider using these websites to opt out of receiving targeted ads:
Using ad blockers with those websites should significantly reduce the number of ads you are exposed to.
7. Block Web Activity Trackers
Ad tracking isn’t the only thing you need to worry about. Websites focus on tracking other things too:
- Your online traffic so that websites know how much time you spend on a platform, what device you are using, and what website pages you engage with.
- How your online activity relates to your social media profile. Facebook pixel is a good example of that since it helps Facebook understand your online behavior so that it can display more “targeted” things in your news feed (including ads).
- What kind of media you enjoy. YouTube does this a lot so that the platform knows what videos to recommend.
- What your current locations is. That kind of info is necessary for platforms that recommend nearby events or give weather forecasts, but it can also just be used for general data tracking and analysis.
Luckily, stopping that is pretty simple – just use Ghostery. It works on nearly all browsers, and it’s very easy to set up.
8. Set Your Social Media Accounts to “Private”
Your social media profiles can leak a lot of sensitive personal information if they are set to public. Think of it – strangers can easily learn a lot of things about your lives just by seeing what you post. That’s why it’s best to make all your accounts private – here are some useful guides for that, in fact:
Also, be really careful with the kind of information you share on social media. It’s best if it’s nothing that could reveal too many details about your personal life (especially your whereabouts).
9. Disable Location Tracking
Pretty much all social media websites or major websites like Google track your device’s location. While they do that to deliver more personalized services, there’s no denying it can feel intrusive and downright creepy. That’s why you should always check account settings to see if it’s possible to turn off Location Tracking/Sharing.

Just keep in mind doing this is not guaranteed to stop platforms and corporations from tracking you all the time. For example, Google recently clarified that even if you turn off Location Tracking services on your Google account, they might still continue to track you (“might” being the keyword). Still, it’s an extra step worth taking.
10. Review Mobile App Permissions
Pretty much every single app you have on your mobile device will require you to give it permission to access at least one of your phone’s functionalities to work. While that does make sense most of the time, it can sometimes become too intrusive – like when apps request access to your real-time location, photos, and contacts.
We recommend checking your mobile device’s App Settings, and revoking any permissions that seem like they’re demanding too much personal information. Some apps should still be able to function even without those permissions.
How to Be Anonymous Online – The Next Level
In this section, we’ll show you how to remain anonymous online using methods that can seem a bit more complex (at least at first). While some time and effort might be required to set everything here up, it can definitely go a long way towards protecting your Internet privacy.
1. Use Signal for Direct Communication
If you’re not familiar with Signal, it’s an online communication app that works on iOS/Android devices and desktop. Its main highlight is the fact that it uses secure end-to-end encryption to protect your text messages and VoIP traffic to ensure that what you talk with someone else stays private.
It’s obviously much better than using Facebook Messenger or Twitter for private conversations since your messages aren’t exposed this way.
You could argue that WhatsApp is a good option too because it actually uses the same type of encryption as Signal. However, the problem with WhatsApp is that it retains metadata, it likely shares user data with Facebook (who now owns WhatsApp), and the way it implements encryption isn’t that foolproof.
So, you’re better off with Signal. Maybe add a VPN in the mix to enjoy even more privacy.
2. Use Encrypted Email Solutions
Not having an email nowadays really isn’t an option, but using the most popular ones (Gmail, Yahoo! Mail or Yandex.Mail) isn’t a good idea – unless you want the service providers to have access to all your email contents, that is.
Tutanota is a pretty good alternative because it comes with a completely encrypted mailbox. Besides that, the company doesn’t log personal information, and only stores IP addresses in an encrypted format which can only be accessed by users themselves. The only drawback is that the free plan only comes with 1GB of storage.
ProtonMail is another decent option. The service offers end-to-end encrypted email accounts, doesn’t require any personal info to set up an account, and the company’s servers are based in Switzerland where they’re protected by favorable privacy laws. Again, though, the free account has more limited storage space (500MB).
Overall, using encrypted email services is just safer. Worst case scenario, if you really must use a popular email service, make sure it’s Gmail and that you use this extension with it since it encrypts your emails.
3. Use Virtual Machine (VM) Software
Simply put, a Virtual Machine emulates a hard drive running an operating system on top of your current operating system. It sounds complex, but it’s pretty easy to run actually – it’s all done through software and an icon on your desktop.
What does this have to do with anonymous browsing, you ask? Well, a VM gives you an extra layer of security when you browse the web since you can connect to the Internet using the VM. Any files you access or download through the VM stay there – they don’t show up on the “host” device.
Thus, it’s easier to avoid being infected with malicious files or malware that could steal sensitive data from you. It’s also highly likely that you could avoid tracking cookies (to a certain extent at least) since they’d just be placed on your VM instead of your “host” device.
VM software is usually free (VirtualBox and VMWare Player), but there are paid options (like VMWare Workstation) too.
4. Use FOSS Instead of Proprietary Software
It’s no longer a secret that the NSA has managed to force numerous tech companies across the globe to build backdoors into their programs. They even managed to “convince” RSA (the company responsible for the world’s most commonly used encryption toolkit) to include security flaws (which the NSA can crack) in their algorithms.
Obviously, proprietary software isn’t that safe anymore – especially given that the NSA can just target the devs if they want to. That’s where FOSS (Free Open Source Software) comes into play – software that’s developed by unconnected individuals with source code that anyone can examine.
Here is a list of a few FOSS examples to get an idea of what’s on offer.
Of course, there’s always a chance the NSA can infiltrate a FOSS community, so it’s always a good idea to be on your guard.
5. Try to Make Anonymous Payments
While you won’t be able to make anonymous payments for physical goods (generally), you might be able to do that with online payments. One of the most common methods to do that is using prepaid cards, but you could also rely on cryptocurrency.
Now, Bitcoin would be the obvious choice – not because of how popular it is, but because it’s one of the more “stable” cryptocurrencies. You should first make an anonymous email account with one of the services mentioned above for buying Bitcoins so that your transactions can’t be traced back to you.

You should try out LocalBitcoins.com since it’s more anonymous (you talk with a seller and arrange a meeting) before going with large platforms like Coinbase or Binance.
Still, keep in mind that Bitcoins are not inherently 100% anonymous. Once you buy them, you still have to use Bitcoin Mixers to “launder” them (it’s basically a process that swaps them with Bitcoins from multiple other users). Of course, Bitcoin Mixers aren’t free, and the fees can be a bit steep.
In case you’d like to learn more about Bitcoin privacy (especially Bitcoin Mixers), feel free to check out ProPrivacy’s guide.
6. Consider Avoiding Windows 10
This piece of advice can seem a bit rough given that Windows 10 is pretty popular nowadays, but the reality is that the operating system is nothing short of a privacy nightmare. For one, there’s a ton of data collection going in the background to the point where a lot of your personal information (activity included) is shared with Microsoft and third parties.
Sure, you can turn the data collection off, but guess what? Even if you do, Windows 10 will still send telemetry data to Microsoft. What’s more, when Microsoft pushed the Anniversary Update back in 2016, they removed the option to disable Cortana, Windows 10’s voice-activated personal assistant that likes collecting a lot of info about you to offer you a more “personalized” experience.
Even more annoying, Microsoft’s Windows 10 updates have a tendency to set your Windows 10 back to its factory settings, meaning you need to tweak the OS privacy settings again and again.
Some obvious alternatives to Windows 10 include Windows XP, 7, and 8 and Mac OS, though Linux distributions are much better choices. If you have no option and really must use Windows 10, consider using W10Privacy (keep in mind it’s not open source software).
Conclusion
All in all, anonymous browsing is something you should strive for if you truly want to protect your online privacy and personal data, and overcome unfair content restrictions. You don’t really have to follow every single piece of advice we offered in this article, but you should at least stick to the ones we mentioned in the “Beginner” section – especially clearing your cache, using ad blockers, using a VPN, and keeping your social media accounts private.
 What Is Deep Packet Inspection?
What Is Deep Packet Inspection?
 Introduction to VPN
Introduction to VPN
